Akira: A Stealthy Ransomware Targeting Unsecured VPNs

Akira ransomware has emerged as a formidable threat in the ever-changing field of cybersecurity. It goes beyond the scope of a regular virus by strategically exploiting weaknesses in Virtual Private Networks (VPNs). Akira uses an attack, combining brute-force attacks and password spying techniques, to specifically target VPNs without Multifactor Authentication (MFA) at the initial access point.
This blog looks into the potentially hazardous realm of Akira ransomware, uncovering its operations and highlighting the concerning strategies used to bypass VPN security.
Crossing Platforms: Akira Ransomware's Dual Assault on Windows and Linux
Type: Ransomware
Type: Ransomware
The Akira ransomware attacks both Linux and Windows systems. Leveraging tools like Any Desk, WinRAR, and PCHunter, this sophisticated attack exploits a critical vulnerability in Virtual Machines (VMs) connected via VPNs without Multifactor Authentication (MFA) and allows unauthorized access to victim data.
After being infiltrated, Akira sets out on a dark attempt to steal sensitive data and encrypt it so that its rightful owner cannot access it. The attacker demands a large ransom to unlock the encrypted data. In a terrible turn of events, victims are put in even more danger and urgency when non-compliance leads to the attackers threatening to expose vulnerable data on the dark web.
Analysis of Akira Ransomware attack:
In the August 2023, threat actors exploited a zero-day vulnerability, CVE-2023-20269, affecting Cisco Adaptive Security Appliance (ASA) and Firepower Threat Defense (FTD) products.
Due to this medium level vulnerability with CVSS score of 5.0, unauthenticated remote attackers were able to establish clientless SSL VPN sessions and compromise credentials using brute-force attacks. This Vulnerability affects Cisco ASA Software Release 9.16 or earlier, emphasizing the critical need for timely software updates for the organizations using these versions.
Infecting Mechanism:
1) Initial access:
Its main objective is to expose VPNs that lack Multifactor Authentication (MFA) as weak points in the network. After entering a target network, the attackers use LSASS (Local Security Authority Subsystem Service) to dump in an attempt to obtain credentials that are essential for breaking into more advanced network layers. They employ brute force techniques, continuously coming up with username and password combinations until the right ones are found. Simultaneously, password spying becomes a powerful tactic in which adversaries try to acquire unauthorized access by comparing popular passwords with a wide range of users.
Akira may also be able to obtain legitimate login credentials from the dark web, an encrypted website known for engaging in illicit activity.
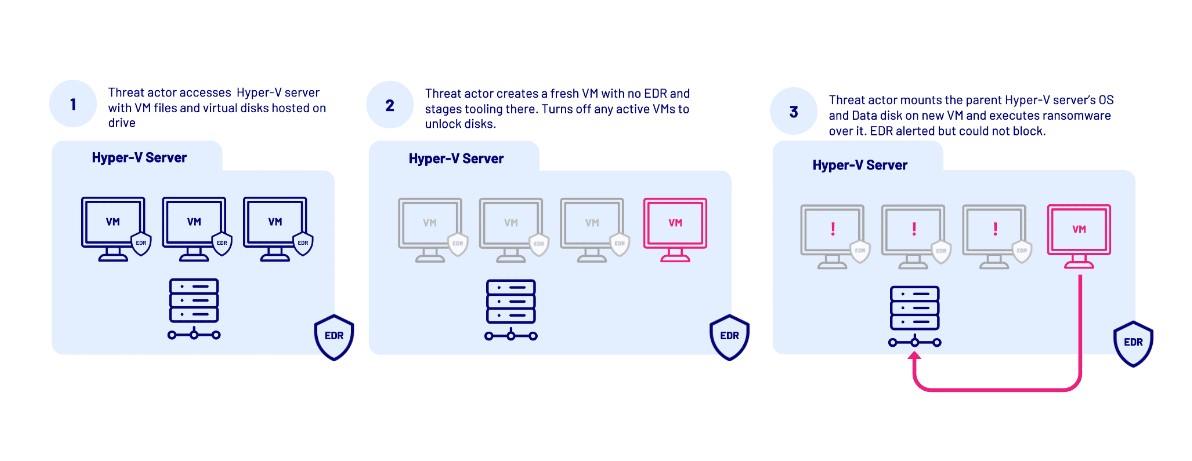
2) Intrusion into Hypervisors:
After entering, the malware targets Windows Hyper-V hypervisors, severely harming any virtual machines linked to the VPN. Threat actors use malicious tactics despite the presence of robust Endpoint Detection & Response (EDR) systems. Then they disable Windows Defender, mount data storage drives on the hypervisor, shut down VMs to release locked disc image files, and launch the ransomware. They install a hidden, unidentified virtual machine on the hypervisor, which gives them the ability to stealthily browse folders and carry out destructive ransomware operations. EDR technologies can identify the encryption process, but they frequently can't stop it from happening inside the virtual machine (VM), which affects systems that are shut down.The attacker's virtual machine, however, is still running and unencrypted.
3) The Final Act of Akira Ransomware
Once the data has been successfully stolen, the attackers take calculated steps to remove Windows Shadow Volume Copies from the targeted device, making recovery unlikely. After there, the ransomware starts to encrypt files on other hard drives by utilizing a predetermined set of extensions. Furthermore, every encrypted file has the unique.akira suffix, designating it as a victim of the Akira ransomware attack.After that the data is encrypted and being kept captive, the attackers issue a dire warning. The decryption key and the safe return of the user's priceless data are requested in exchange for a sizable ransom. A terrifying threat that the possible release of the compromised data on the dark web is implied in this demand.
Safeguarding Against Ransomware Attacks: Essential Best Practices:
- Maintain offline backups and keep them up to date
- All the Applications, OS must be updated regularly along with virtual patching to protect networks and legacy systems.
- Implement strong password policies across systems and applications.
- Enforce Multi Factor Authentication (MFA) to add an extra layer of security.
- Perform Vulnerability Assessment and Penetration Testing (VAPT) regularly.
- Conduct security audits on critical networks and systems to identify and address vulnerabilities.
- Establish Domain-based Message Authentication, Reporting and Conformance (DMARC).
- Implement Sender Policy Framework (SPF) for your domain to prevent email spoofing.
References:
- Virus alerts akira ransomware
- Akira Ransomware Targeting VPNs without Multi-Factor Authentication - Cisco Blogs
- Weaponising VMs to bypass EDR - Akira ransomware | CyberCX
Contact
For more information on how we can help you secure your data, get you compliant and protect your business, please complete the form below and one of Information security / Cyber Forensic expert and Compliance specialists will respond to you as soon as possible.


